Cybersecurity teams are constantly faced with the challenge of managing and responding to an increasing number of security incidents. To tackle this issue efficiently, organizations require powerful and integrative tools that can automate workflows and facilitate seamless coordination between different security tools and APIs. Python's flexibility and integration capabilities make it an ideal language for building security orchestration and incident response platforms.
This article explores the reasons why this programming language is particularly well-suited for this purpose and highlights its potential benefits for cybersecurity with Python.
Automated Threat Detection and Response
With the help of libraries like Requests and BeautifulSoup, the system can retrieve information from websites or APIs, allowing it to gather the necessary data for analysis and monitoring. This capability is particularly useful when monitoring network traffic, system logs, and other data sources that contain vital information about potential threats.
Libraries and APIs also facilitate the automation of the detection of suspicious activities. Libraries such as Scapy or Pyshark provide functionalities that enable the extraction of specific packet information, such as source IP addresses, destination ports, or protocol types. By combining this information with predefined patterns or behavioral models, you can automatically flag potential threats and anomalies.
Once suspicious activities are detected, Python in security enables immediate response actions to be triggered. With the help of libraries like Paramiko or Netmiko, you can establish SSH or Telnet connections to various devices, such as firewalls or routers, and perform actions like blocking IP addresses, updating access control lists, or generating alerts. This level of automation not only saves time and effort but also ensures that response actions are executed promptly, reducing the window of opportunity for potential attackers.
Furthermore, the simplicity makes it accessible to both experienced professionals and those new to the field. Its clean syntax and extensive documentation make it easy to develop, understand, and maintain scripts and applications. This accessibility of Python for security professionals enables intelligent monitoring and response actions, even if they do not have an extensive background in programming.
Machine Learning and AI
Python's popularity has skyrocketed in recent years as a preferred programming language in the field of ML and AI. One significant reason behind its rise is the extensive ecosystem of libraries designed for these domains. Among these libraries, TensorFlow and Scikit-learn have emerged in implementing advanced algorithms. Leveraging their capabilities, Python in cybersecurity enables the analysis of vast amounts of data and enhances real-time anomaly detection.
TensorFlow
TensorFlow is an open-source library developed by Google that specializes in deep learning, making it highly suitable for many cutting-edge applications. It offers a flexible and efficient computational framework for implementing complex ML models, such as neural networks. TensorFlow allows to train and deploy models capable of analyzing vast amounts of data to identify and understand threats.
Enhanced Anomaly Detection
Security algorithms based on TensorFlow can learn and adapt to different user behavior patterns or characteristics. By utilizing deep neural networks, TensorFlow can process data with multiple layers of abstraction, allowing it to identify and detect anomalies more accurately. Whether it is fraudulent user activities, TensorFlow's advanced algorithms can uncover subtle patterns that traditional methods might miss.
Real-time Threat Identification
One of Python cybersecurity examples is real-time threat identification that is crucial for timely response and mitigation. TensorFlow's distributed computing capabilities enable the implementation of algorithms that can handle the massive volumes of data encountered in applications.
Scikit-learn
The library is renowned for its user-friendly nature and extensive collection of ML algorithms. Although it may not focus specifically on deep learning like TensorFlow, scikit-learn offers a broad range of traditional ML algorithms that can be effectively employed for Python in security.
Feature Extraction and Selection
In applications, analyzing large amounts of data is paramount. Scikit-learn's feature extraction and selection techniques help in identifying relevant features from vast datasets. These techniques enable professionals to reduce the dimensionality of data, improving algorithm performance and enhancing anomaly detection accuracy.
Classification and Clustering
Scikit-learn provides a diverse set of classification and clustering algorithms that can be utilized to categorize and group data. For instance, these algorithms can be applied to classify potentially malicious network traffic patterns, detect spam messages or email phishing attempts. The ability to classify and cluster data in real-time using scikit-learn empowers systems to quickly adapt and defend against evolving threats.
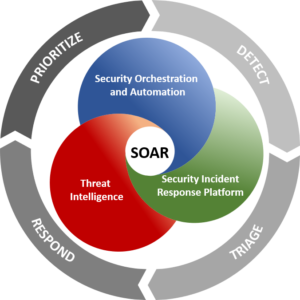
Security Orchestration and Incident Response
Custom Workflow Creation
The simplicity and versatility allow cybersecurity teams to leverage its capabilities for creating custom workflows tailored to their specific needs. This flexibility enables the development of incident response processes that align with an organization's unique requirements. By scripting and orchestrating complex tasks using code, teams can streamline their operations and ensure consistent response across incidents. The readability and vast library ecosystem make it straightforward to implement various actions and steps within an incident response workflow, such as data enrichment, threat analysis, and containment.
Automation of Incident Response Actions
The rich libraries and modules allows cybersecurity teams to automate incident response actions effectively. With Python, teams can develop scripts to automate and execute repetitive tasks, freeing up valuable time for analysts to focus on more critical aspects of incident response. One of Python cybersecurity examples can be scripts that can be employed to automatically collect and analyze log data, perform system checks, communicate with tools and APIs, and generate incident reports. The ability to automate these actions drastically reduces manual effort, improves consistency, and accelerates incident resolution.
Integration with Security Tools and APIs
This integration potential allows Python-based incident response platforms to interact with diverse cybersecurity solutions, including SIEMs, threat intelligence databases, vulnerability scanners, endpoint protection solutions, and many more. By integrating with these tools, Python-based platforms can leverage their capabilities to enhance threat detection, containment, and response efficiency. The integration capabilities enable the transfer of information between tools, the orchestration of actions, and the retrieval and analysis of data, ultimately improving overall incident response effectiveness.
Extensibility and Community Support
The vibrant and extensive open-source community provides a vast pool of resources, community-contributed modules, and documentation. This community support greatly assists in accelerating the development and maintenance of security orchestration. The availability of pre-built Python libraries relevant to cybersecurity, such as requests, paramiko, and pytz, simplifies the implementation of essential actions like remote commands execution, API communication, time zone conversions, and encryption. Furthermore, the community of Python in security actively contributes to enhancing security-related modules, ensuring that security orchestration and incident response platforms have access to the latest tools and capabilities.
Secure Code Development and Auditing
One of the key advantages of using Python for cybersecurity development is its emphasis on readability. This readability contributes to the maintainability of code, a crucial factor in ensuring its safety. When code is easy to read and understand, developers are more likely to spot potential vulnerabilities and address them effectively.
Some capabilities play a significant role in enhancing the security of code. The language provides a robust testing framework called unittest, which allows developers to create test cases for their code. With unittest, developers can write test code to verify the behavior of their functions, classes, and modules. These tests can include specific scenarios to validate that code is secure and not susceptible to common vulnerabilities.
Moreover, the inner ecosystem offers a variety of third-party testing libraries that further extend its testing capabilities. One such library is pytest, which streamlines the testing process by providing more concise and expressive syntax for writing tests. Pytest also offers a wide range of plugins that can be leveraged for specific tests, enabling developers to identify vulnerabilities early in the development cycle.
In addition to testing frameworks, the ecosystem includes various libraries focused on security. For example, Bandit is a popular Python for cybersecurity linter that scans code for common issues. It performs static analysis to identify potential vulnerabilities, such as insecure input handling, code injection, or lack of proper access controls. Using Bandit as part of the development process allows developers to catch and address issues before code is deployed.
Another notable library is Pyre-check, a static type checker. Pyre-check enforces type annotations and performs deep analysis of the codebase. This helps identify potential type-related security vulnerabilities, such as the misuse of sensitive data or the unintentional exposure of private information. By utilizing Pyre-check, developers can catch type-related security issues and prevent them from becoming exploitable vulnerabilities.
The combination of readability, built-in testing capabilities, and its ecosystem of testing frameworks and security libraries makes it an ideal choice for security-minded developers. The language's readability allows for easier code review and understanding, while the testing frameworks provide a solid foundation for testing code and ensuring its security. Additionally, third-party libraries like Bandit and Pyre-check offer specialized tools for identifying and mitigating various security vulnerabilities.
Threat Hunting and Forensics
One of the libraries that makes Python a valuable asset in threat hunting and digital forensics is Volatility. Volatility is an open-source memory forensics framework that allows cybersecurity professionals to examine the contents of a computer's volatile memory. This is particularly useful in incident response and digital forensics investigations, as volatile memory often contains valuable information about running processes, network connections, and potentially malicious activity. By utilizing Python and Volatility, analysts can write custom scripts to extract and analyze data from memory dumps, helping them uncover hidden threats and understand attacker techniques.
Another library that enhances capabilities in threat hunting and digital forensics is pytsk3. Pytsk3 is a Python binding for the Sleuth Kit (TSK), a popular digital forensics toolkit. It provides a wide range of functionalities for accessing and analyzing file systems from disk images, such as NTFS, FAT, and EXT. With pytsk3, professionals can write Python security scripts to automate the extraction of evidence from disk images, enabling them to identify malicious files, uncover hidden directories, and trace attacker activities. This powerful combination of Python and pytsk3 allows analysts to efficiently parse and examine file systems, making their investigations more thorough and effective.
The versatility of Python in cybersecurity extends beyond memory forensics and disk image analysis. By harnessing the power of the code, analysts can extract valuable information from log files, correlate events, detect patterns, and identify anomalous behavior. This capability of Python for cybersecurity to handle such targeted analysis of structured data further enhances its value in threat hunting and cybersecurity investigations.
Conclusion
Python's extensive libraries and APIs provide security professionals with a myriad of tools to automate the monitoring of network traffic, system logs, and other data sources. These resources enhance the recognition of suspicious activities and enable immediate response actions, ultimately bolstering the overall security posture. Additionally, seeking the assistance of a custom software services provider can significantly boost the efficiency of the software development process, ensuring the delivery of robust and tailored solutions that address the specific needs of cybersecurity professionals.